利用k8s审计日志生成RBAC规则
简介
很多时候我们在k8s上安装服务会遇到各种各样的权限问题,有时候为某个用户或者serviceaccount对象生成一个合适的role会比较头疼,这里推荐一个工具audit2rbac,它可以根据k8s的审计日志,为指定用户或者serviceaccount对象生成它们所需要的role.
audit2rbac下载地址: https://github.com/liggitt/audit2rbac/releases
前提要求
1、集群已经开启审计日志,且日志格式为json格式,开启审计日志可以参考https://kubernetes.io/docs/tasks/debug-application-cluster/audit/#advanced-audit
2、建议日志级别设置为Metadata,还可以减少日志大小
使用
我们这里已经开启了审计日志,这里截取一小段日志内容如下:
1 | {"kind":"Event","apiVersion":"audit.k8s.io/v1","level":"Metadata","auditID":"571b8d06-aa30-4aec-87cb-7bef2ef88d18","stage":"ResponseComplete","requestURI":"/apis/coordination.k8s.io/v1/namespaces/longhorn-system/leases/external-resizer-driver-longhorn-io","verb":"update","user":{"username":"system:serviceaccount:longhorn-system:longhorn-service-account","uid":"cdb0a05f-170d-4f02-aeec-88af904e68f7","groups":["system:serviceaccounts","system:serviceaccounts:longhorn-system","system:authenticated"]},"sourceIPs":["172.20.166.16"],"userAgent":"csi-resizer/v0.0.0 (linux/amd64) kubernetes/$Format","objectRef":{"resource":"leases","namespace":"longhorn-system","name":"external-resizer-driver-longhorn-io","uid":"81766194-e2e3-4edd-83d7-788a07562b91","apiGroup":"coordination.k8s.io","apiVersion":"v1","resourceVersion":"18772044"},"responseStatus":{"metadata":{},"code":200},"requestReceivedTimestamp":"2021-01-06T03:02:52.709670Z","stageTimestamp":"2021-01-06T03:02:52.710917Z","annotations":{"authorization.k8s.io/decision":"allow","authorization.k8s.io/reason":"RBAC: allowed by ClusterRoleBinding \"longhorn-bind\" of ClusterRole \"longhorn-role\" to ServiceAccount \"longhorn-service-account/longhorn-system\""}} |
接下来我们使用audit2rbac为serviceaccount:longhorn-system:longhorn-service-account生成rbac role
1 | [root@master-01 audit2rbac]# ./audit2rbac -f /var/log/kube-audit/audit-log.json --serviceaccount longhorn-system:longhorn-service-account > longhorn-service-account-role.yaml |
查看一下生成的role
1 | apiVersion: rbac.authorization.k8s.io/v1 |
可视化集群中的rbac
rback可以使用Kubernetes集群的所有与RBAC相关的信息去生成service account,roles,和访问规则之间的关系图
安装
1 | curl -sL https://github.com/team-soteria/rback/releases/download/v0.4.0/linux_rback -o rback |
使用
我们可以在本地运行并输出为result.dot文件,利用该文件可以在线或者本地渲染图形
1 | kubectl get sa,roles,rolebindings,clusterroles,clusterrolebindings --all-namespaces -o json | rback > result.dot |
在线渲染
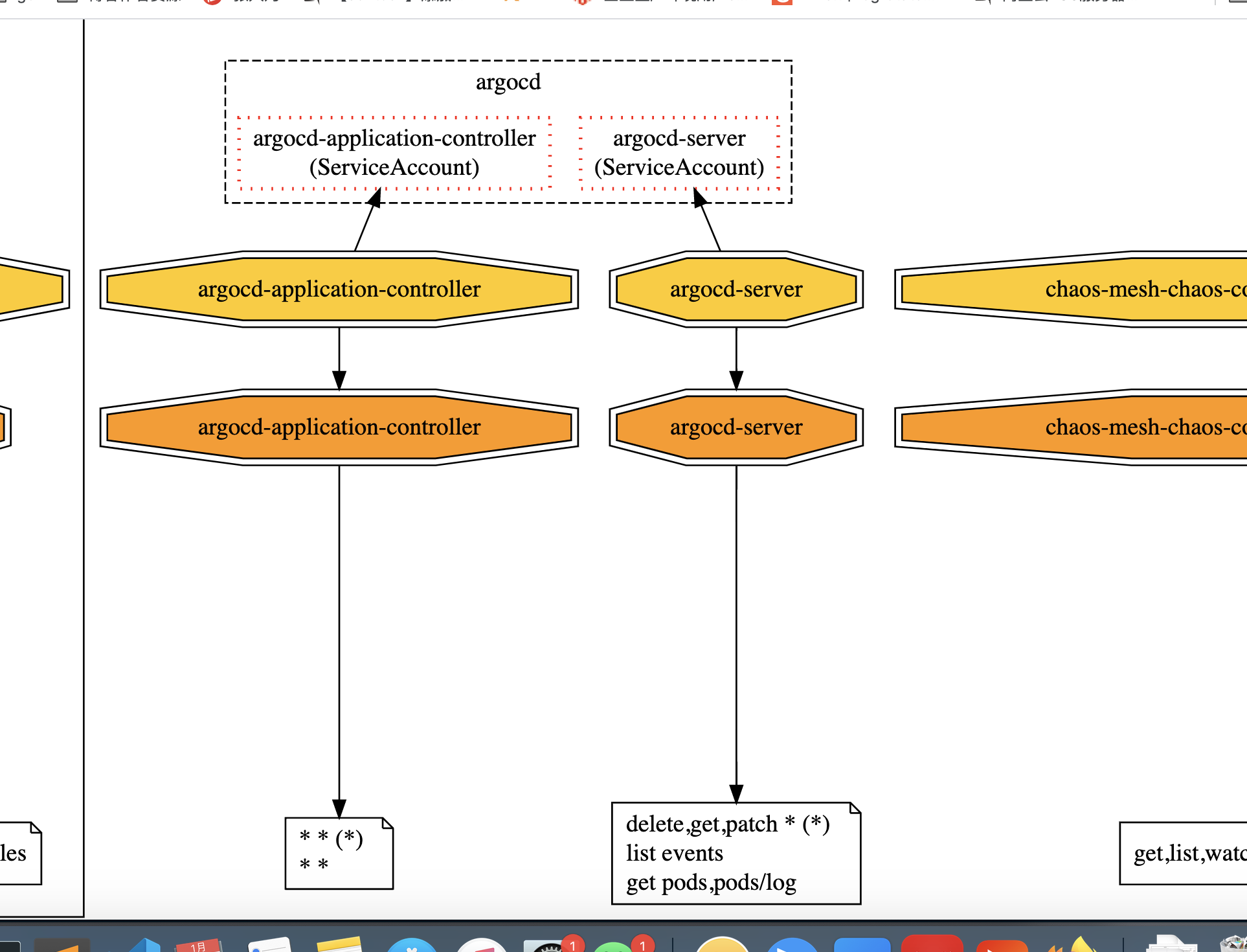
有许多Graphviz(dot)在线可视化工具可用,例如,使用magjac.com/graphviz-visual-editor/和dreampuf.github.io/GraphvizOnline
我们打开result.dot,把文件内容复制到上面网站即可
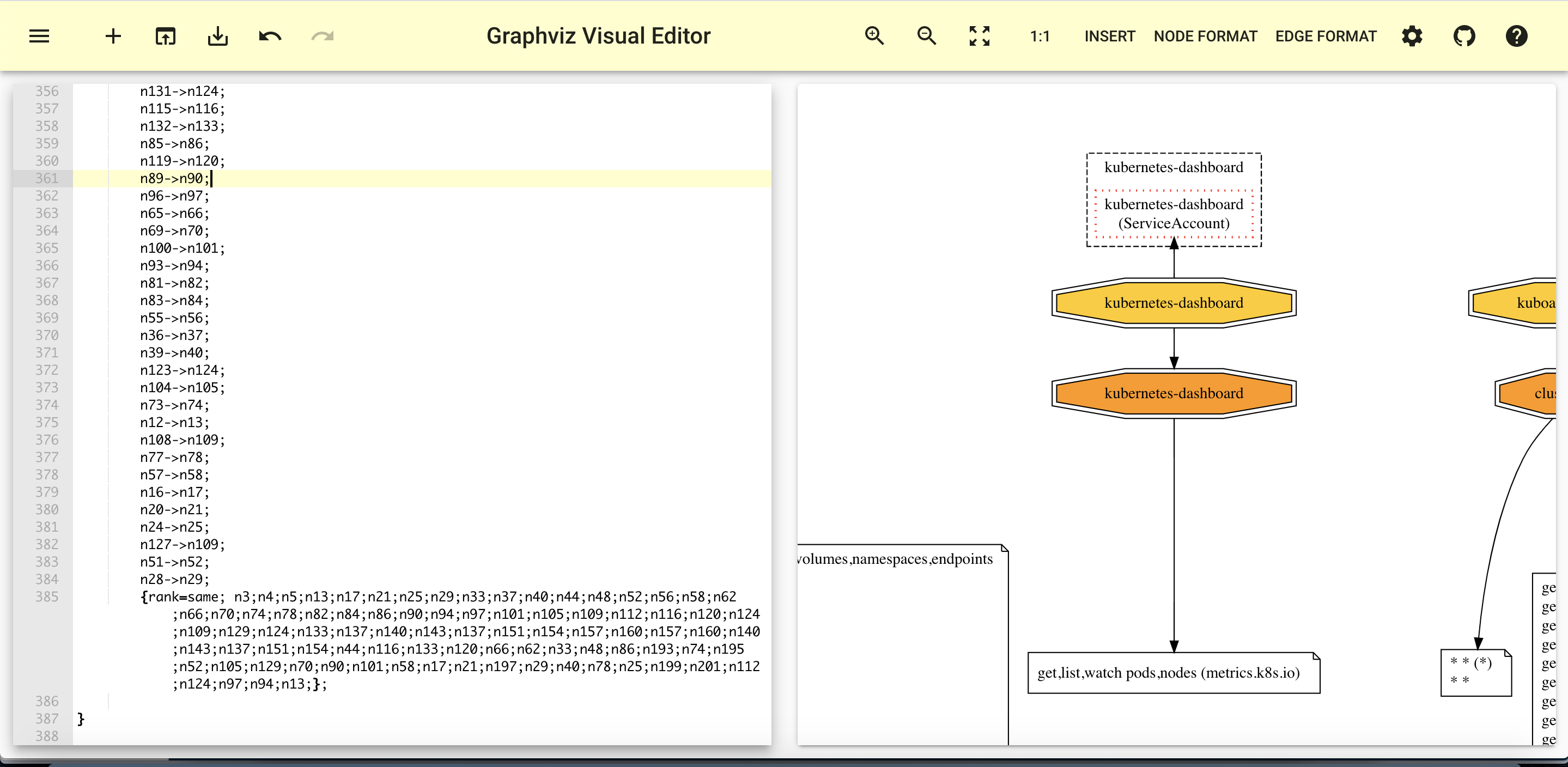
这里节选一部分下载到本地的图形(展示所有namespace中图形太长了)
本地渲染
这里以mac上操作示例
安装graphviz brew install graphviz,然后执行下面操作
1 | kubectl get sa,roles,rolebindings,clusterroles,clusterrolebindings --all-namespaces -o json | rback | dot -Tpng > /tmp/rback.png && open /tmp/rback.png |
使用rbac-lookup查看集群内rbac绑定
简介
RBAC Lookup 是一个 CLI,可让您轻松查找绑定到任何用户、service accout 、group的 Kubernetes roles 和 cluster roles 。
安装
到https://github.com/FairwindsOps/rbac-lookup/releases页面下载
1 | wget https://github.com/FairwindsOps/rbac-lookup/releases/download/v0.6.4/rbac-lookup_0.6.4_Linux_x86_64.tar.gz |
使用
1 | [root@master-01 permission-manager]# rbac-lookup -h |
我们可以查看特定用户、service accout 、group绑定的role
1 | [root@master-01 permission-manager]# rbac-lookup lishuai |
-o wide 选项可以输出更多信息
1 | [root@master-01 permission-manager]# rbac-lookup lishuai -o wide |
也可以按RBAC Subject类型进行分类,参数--kind or -k 可以接受user,group和serviceaccount作为值。
1 | [root@master-01 permission-manager]# rbac-lookup li --output wide -k serviceaccount |