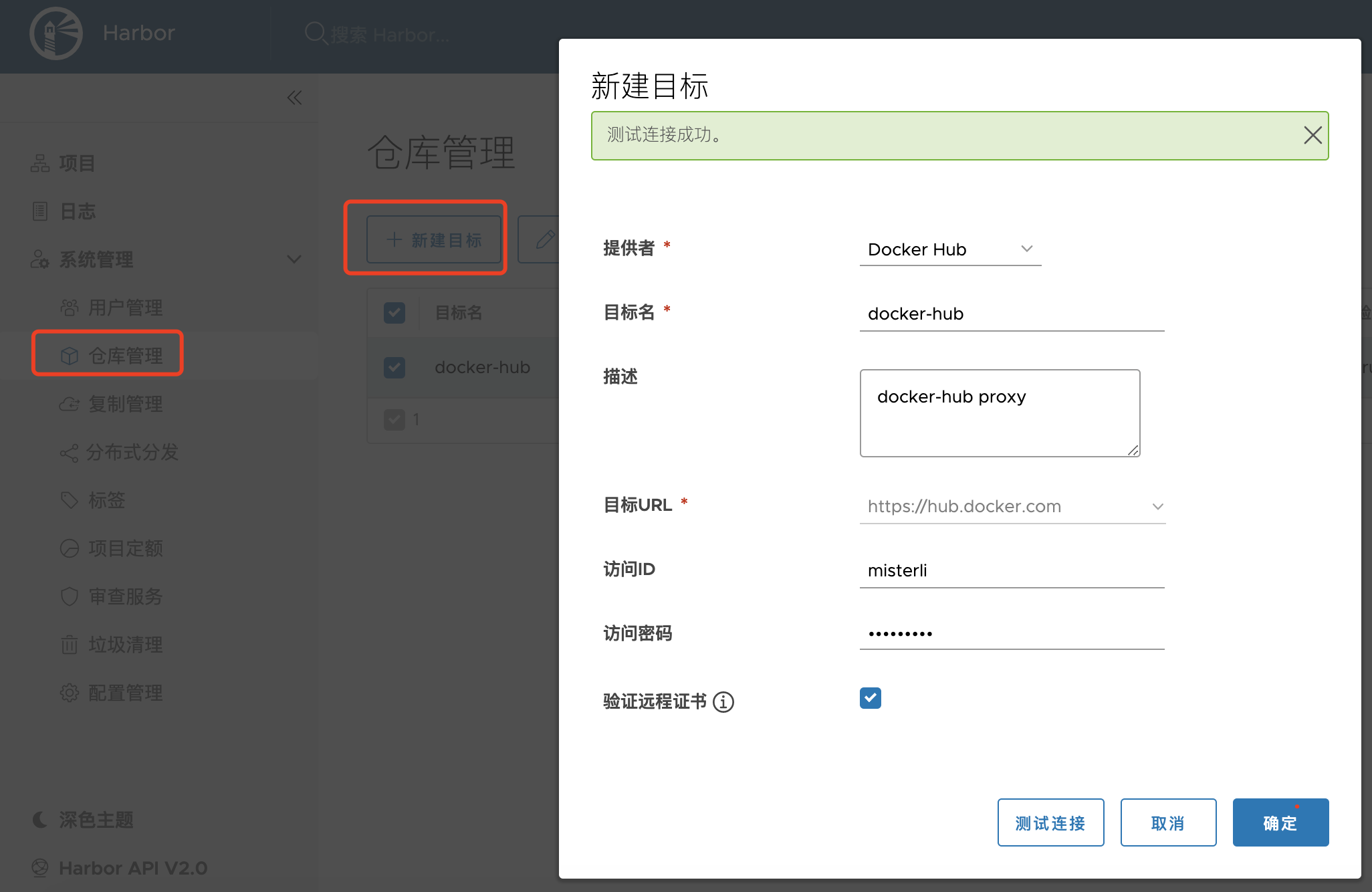
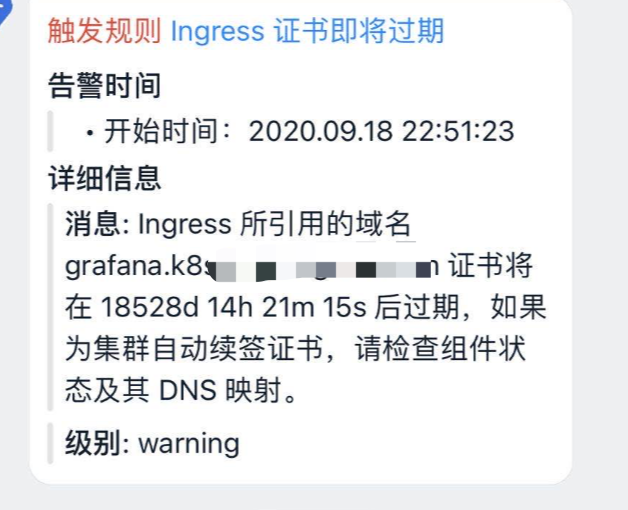
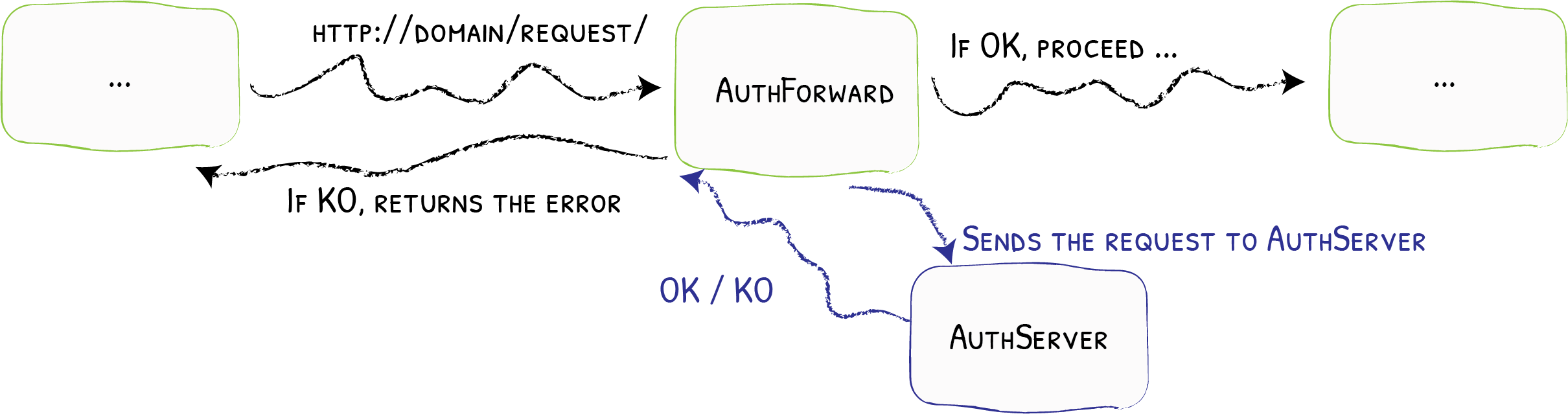
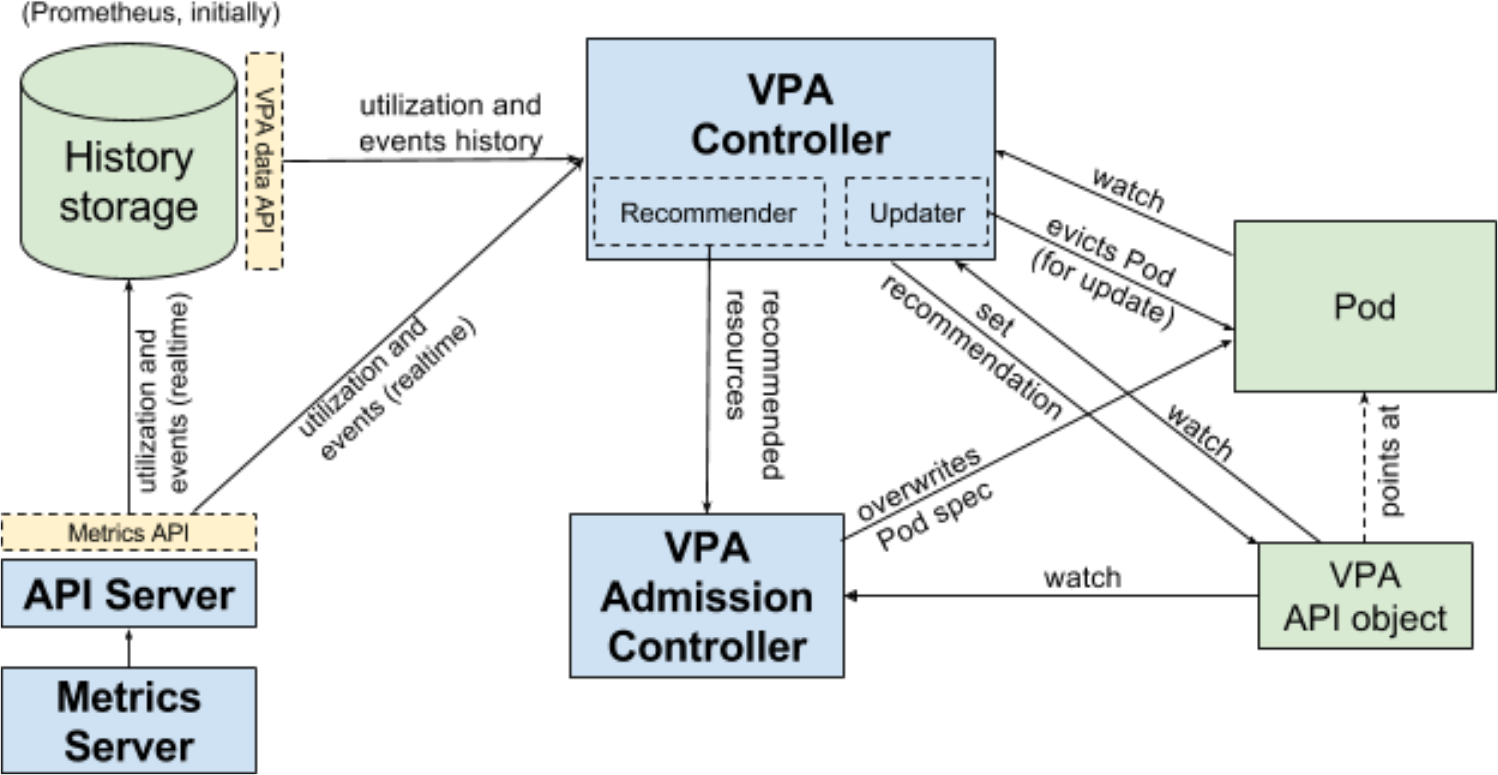
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| I0920 21:36:32.855359 1 controller.go:170] cert-manager/inject-controller "level"=1 "msg"="updated object" "resource_kind"="APIService" "resource_name"="v1beta1.webhook.cert-manager.io" "resource_namespace"=""
I0920 21:36:32.855410 1 controller.go:242] cert-manager/controller-runtime/controller "level"=1 "msg"="Successfully Reconciled" "controller"="apiservice" "request"={"Namespace":"","Name":"v1beta1.webhook.cert-manager.io"}
E0920 21:36:32.855257 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dashboard-tls\" not found" "certificate"={"Namespace":"kube-system","Name":"com-dashboard-tls"} "secret"={"Namespace":"kube-system","Name":"com-dashboard-tls"}
E0920 21:36:32.855516 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dashboard-tls\" not found" "certificate"={"Namespace":"kube-system","Name":"com-dashboard-tls"} "secret"={"Namespace":"kube-system","Name":"com-dashboard-tls"}
E0920 21:36:32.855690 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dashboard-tls\" not found" "certificate"={"Namespace":"kube-system","Name":"com-dashboard-tls"} "secret"={"Namespace":"kube-system","Name":"com-dashboard-tls"}
E0920 21:36:32.855742 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dashboard-tls\" not found" "certificate"={"Namespace":"kube-system","Name":"com-dashboard-tls"} "secret"={"Namespace":"kube-system","Name":"com-dashboard-tls"}
E0920 21:36:32.856413 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.856444 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.856578 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.856607 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.856710 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.856745 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.856793 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.856881 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0920 21:36:32.857349 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.857377 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.857427 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.857456 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.857630 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.857728 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.857764 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.857809 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-job-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-job-tls"}
E0920 21:36:32.858259 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.858287 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.858358 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.858443 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.858480 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.858535 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.858641 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.858666 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-dataworks-tls\" not found" "certificate"={"Namespace":"dataworks","Name":"com-dataworks-tls"} "secret"={"Namespace":"dataworks","Name":"com-dataworks-tls"}
E0920 21:36:32.859427 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0920 21:36:32.859457 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0920 21:36:32.859508 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0920 21:36:32.859538 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0920 21:36:32.859636 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0920 21:36:32.859659 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0920 21:36:32.859727 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0920 21:36:32.862350 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"cn-grafana-tls\" not found" "certificate"={"Namespace":"monitoring","Name":"cn-grafana-tls"} "secret"={"Namespace":"monitoring","Name":"cn-grafana-tls"}
E0921 03:50:36.814654 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0921 03:50:36.814654 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0921 03:50:36.814747 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
E0921 03:50:36.814748 1 indexers.go:93] cert-manager/secret-for-certificate-mapper "msg"="unable to fetch certificate that owns the secret" "error"="Certificate.cert-manager.io \"com-kibana-tls\" not found" "certificate"={"Namespace":"elastic","Name":"com-kibana-tls"} "secret"={"Namespace":"elastic","Name":"com-kibana-tls"}
|